The world is influenced by major businesses and tech companies. Technological advancements have made the functioning of various industries efficient. There is a negative aspect to everything. With the increase in technology and productivity, companies have become vulnerable to threats. There has been a significant rise in cyber threats in recent times. Cyber threats aim to jeopardize a company’s operations and revenue. These are just like natural calamities, and it is important to stay prepared with effective preventive measures. How do companies overcome these challenges? Companies implement incident response planning to minimize the damage during times of hardship.
In this article, we will discuss more on these strategies and how they help companies stay in a secure spot:
What is Incident Response Planning?

Incident response is a strategic process an organization follows at the time of a security breach. An incident response plan includes a set of written instructions that outlines the planned procedures to reduce the damage and recovery time after a cyber attack or data breach. An IT professional is in charge of designing and using incident response plans and aims to reduce the aftermath effect of data leaks.
Why are Incident Response Plans Important?
With the increased rate of cyber attacks, it has become challenging for companies and organizations to safeguard their information and retaliate. They cause immense damage to a company by affecting its brand reputation, intellectual property, and loss of time and revenue.
Incident response planning plays an important role in improving a company’s defense mechanism. They help minimize the impact of security breaches, save time in fixing the vulnerabilities, and lower expenses. Robust response planning helps companies quickly recover from attacks and ensures only minimal disruption to operations. Well-designed response plans can identify vulnerabilities in a company and help improve the overall security and defense mechanism.
Most Common Types of Cyber Attacks

The frequency of cyber attacks is increasing. With the advancements in technology, hackers are using more effective hacking techniques to alter the functions of an organization.
Here are the three most common cyber attacks:
- Phishing Attacks: Phishing is one of the most common cyber attacks. It occurs when a hacker sends emails that appear to be from a trusted and legitimate source. The emails contain links that trick the users into downloading malicious software.
- Whale-Phishing Attacks: The main motive of these attacks is to target big shorts or the Whale of an organization. When the malicious software is downloaded, hackers access the confidential information of an organization and demand ransom.
- Ransomware: As the name suggests, the firewall system of an organization is held hostage until the ransom is paid. The malicious software is installed through spoof emails. The hackers are exposed to all the vulnerabilities of an organization and demand money in return for the decrypted code to access the firewall.
Computer Security Incident Team (CSIRT)
Organizations have different teams to ensure the overall efficiency of the operations. The IT team plays a crucial role in safeguarding the confidential data, intellectual property, and firewall system of an organization. A computer security incident team (CSIRT) consists of these officials, and they are responsible for handling the incident response process. CSIRT’s core role is to protect the Confidentiality, Integrity, and Availability (CIA) of business assets. The main role is handled by one or more people. The senior and executive management are given the task of making critical decisions, while the incident manager makes sure that the stakeholders are aware of the incident. The CSIRT consists of analysts, IT techs, and security breach investigators. They collaborate with teams like human resources, law enforcement, and public relations.
Major Steps To Devise Incident Response Plans
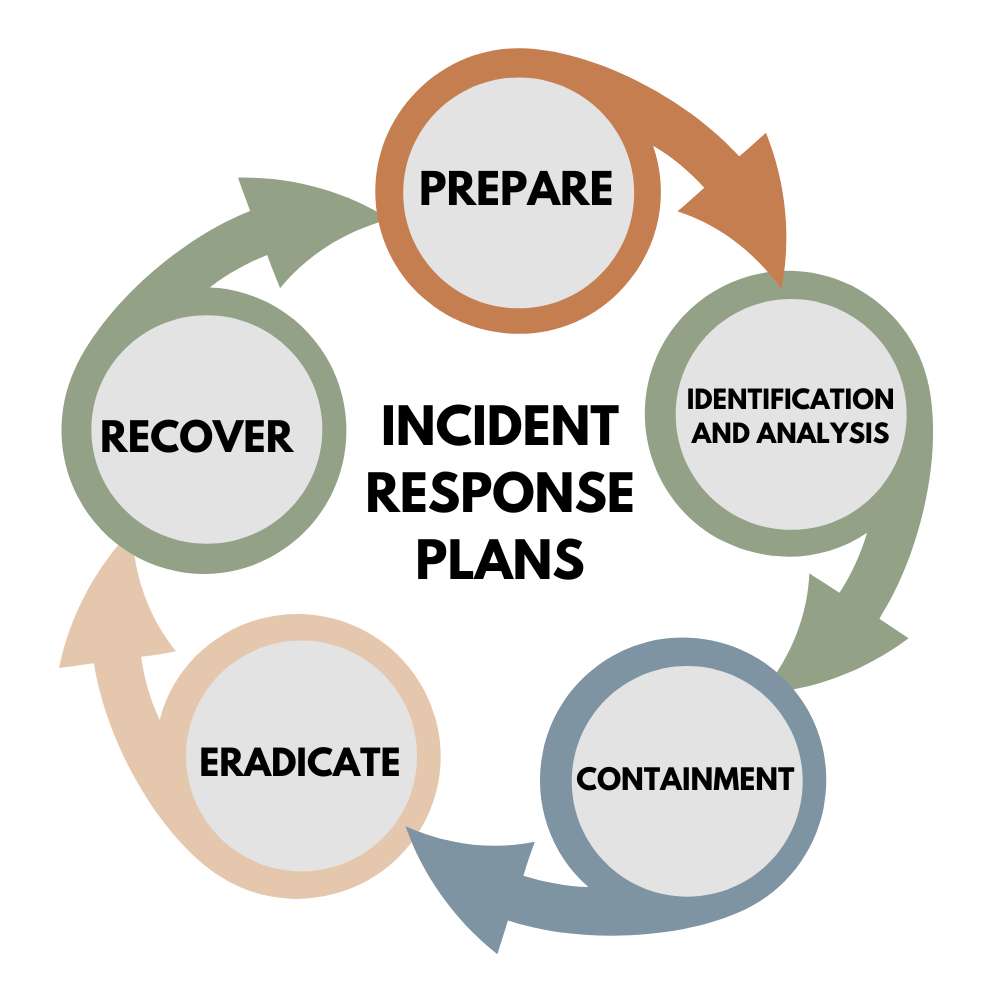
To maintain the smooth functioning of operations, companies must implement effective incident response planning strategies to safeguard their intellectual properties.
Whatever the method may be, the inclusion of these five steps is important, and they are:
1. Prepare
Preparation is one of the key steps in the incident response planning process, as it determines how well an organization responds to security breaches. Malicious activities can be of different forms and lead to a sharp fall in profits. Develop a strong policy consisting of rules and principles to be followed at the time of malicious activity. Make sure that the incidents are documented and accurately communicated with the investors and stakeholders.
2. Identification and Analysis
The second step involves the process of detecting possible data breaches. To get a clear conclusion, gathering information such as error messages, log files, intrusion detection, and firewall systems is important. The CSIRT must be informed of the anomalies as quickly as possible. They analyze the threat targeting the vulnerable segments and take effective measures to prevent it.
3. Containment
Incident response planning includes the identification of threats. Once a threat has been identified, an organization must try to prevent and limit the damage.
This can be done by following three steps, and they are:
- Short-term containment– It involves taking swift measures like taking down the server of the affected system and directing the traffic to an alternate server.
- System Back-up– Make sure that the confidential data is backed up in a failsafe system.
- Long-term containment– Organizations can’t afford to stop their operations as it will lead to huge losses. For that to happen, the affected systems are temporarily fixed while rebuilding the new ones.
4. Eradicate
Eradication is an integral part of incident response planning. This step involves the process of removal of malicious software and restoring the systems. The documentation for this process must be right and accurate as it determines the costs and resources used to eradicate the malware. Eradication plays a crucial role as it helps an organization understand and fix its vulnerabilities.
5. Recover
Disruption of a system results in slow operations and incident response planning is time taking. Once the systems are affected, organizations take some time to bounce back onto the track. This step involves slowly bringing back the affected systems into the production process. Before bringing them back into production, it is important that they must be tested.
Summing Up
Technology is shaping up the functionality of the world. Many industries are harnessing the power of tech to increase productivity. With the ongoing competition to stand out, there occurs a risk of compromising intellectual properties. This is done through cyber threats. Cyber threats aim to retrieve the sensitive information of organizations and jeopardize the operation and revenue. It is important that organizations design effective incident response planning strategies to minimize the impact of cyber threats. These plans help in identifying and eradicating the threats for smooth functioning.







